Overview
SSO/SAML is only available on Production and Enterprise plans.
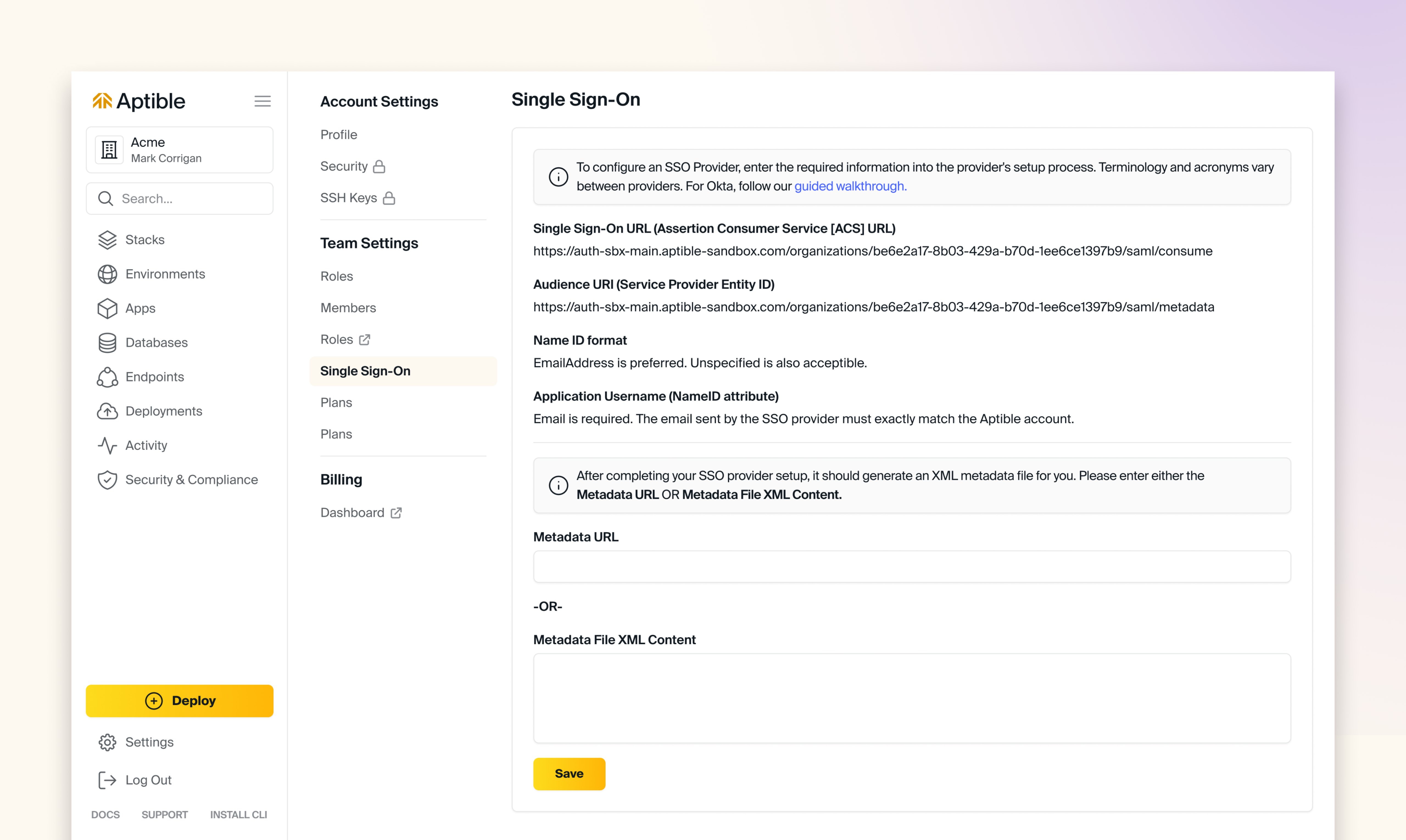
How to setup Single Sign-On (SSO)
Organization Login ID
When you complete Single Sign On Provider Setup, your organization’s users can use the SSO link on the SSO login page to begin using the configured SSO provider. They must enter an ID unique to your organization to indicate which organization they want to access. That ID defaults to a randomly assigned unique identifier. Account owners may keep that identifier or set an easier-to-remember one on the SSO settings page. Your organization’s primary email domain or company name makes a good choice. That identifier is to make login easier for users. You will have to distribute the ID to your users so they can enter it when needed. To simplify this, you can embed the ID directly in the URL. For example,https://dashboard.aptible.com/sso/example_id. Users can then bookmark or link to that URL to bypass the need to enter the ID manually. You can start the login process without knowing your organization’s unique ID if your SSO provider has an application “dashboard” or listing.
Require SSO for Access
WhenRequire SSO for Access is enabled, Users can only access their organization’s resources by using your configured SAML provider to authenticate with Aptible. This setting aids in enforcing restrictions within the SSO provider, such as password rotation or using specific second factors.
Require SSO for Access will prevent users from doing the following:
- Users cannot log in using the Aptible credentials and still access the organization’s resources.
- Users cannot use their SSH key to access the git remote.
CLI Token for SSO
To use the Aptible CLI with Require SSO for Access enabled, users must:- Generate an SSO token.
- In the Aptible Dashboard, select the user’s profile on the top right and then “CLI Token for SSO,” which will bring you to the CLI Token SSO settings page.
- Provide the token to the CLI via the
aptible login --sso $SSO_TOKENcommand.
Invalidating CLI Token for SSO
- Tokens will be automatically invalidated once the selected duration elapses.
- Generating a new token will not invalidate older tokens.
- To invalidate the token generated during your current session, use the “Logout” button on the bottom left of any page.
- To invalidate tokens generated during other sessions, except your current session, navigate to Settings > Security > “Log out all sessions”
Exempt Users from SSO Requirement
Users exempted from the Require SSO for Access setting can log in using Aptible credentials and access the organization’s resources. Users can be exempt from this setting in two ways:- users with an Account Owner role are always exempt from this setting
- users added to the SSO Allow List
Require SSO for Access is enabled.
We recommend restricting the number of Users exempt from the Require SSO for Access settings, but there are some use cases where it is necessary; some examples include:
- to allow users to use their SSH key to access the git remote
- to give contributors (e.g., consultants or contractors) access to your Aptible account without giving them an account in your SSO provider
- to grant “robot” accounts access to your Aptible account to be used in Continuous Integration/Continuous Deployment systems

